Although nowadays HDD space is a cheap commodity there is always a Windows C:\ running somewhere with a partition that is busting at the seams and ready to explode. I’ve seen it too many times…
As there are a number of common culprits for these space eating monsters I’m going to post the fixes here in one sweet spot, the “Windows System Cleanup” post.
Windows “Hiberfil.sys”
Hibernate mode uses the hiberfil.sys file to store the current state (memory) of the PC on the hard drive and the file is used when Windows is turned back on.
Always a cause of taking up C:\ the easiest option is to switch it off. Use the following command line to disable:
Enter "powercfg.exe -h off"
Pagefile.sys is a windows system file used as a swap file and was designed to improve performance. Windows uses it as memory location in case the application you’re running ends up needing more RAM than you actually have. This file is stored on the C:\ root but can take up space. Best option is to move it or reduce it (Reducing isn’t really a recommended option)
- Right click on ‘PC’.
- Left click on ‘Properties’.
- Left click on ‘Advanced system configuration’.
- If needed, left click on ‘OK’.
- Select ‘Advanced options’ tab.
- Left click on ‘Configuration’ inside ‘Throughput’.
- Select ‘Advanced options’ tab.
- Left click on ‘Change’ inside ‘Virtual memory’.
- Edit your preferences.
- Close all the opened windows by accepting.
Windows “Search” Folder
?
Windows “WINSXS” Folder
Reference this post: Saving Windows Disk Space | Reducing Size of WINSXS folder | Server 2008 R2
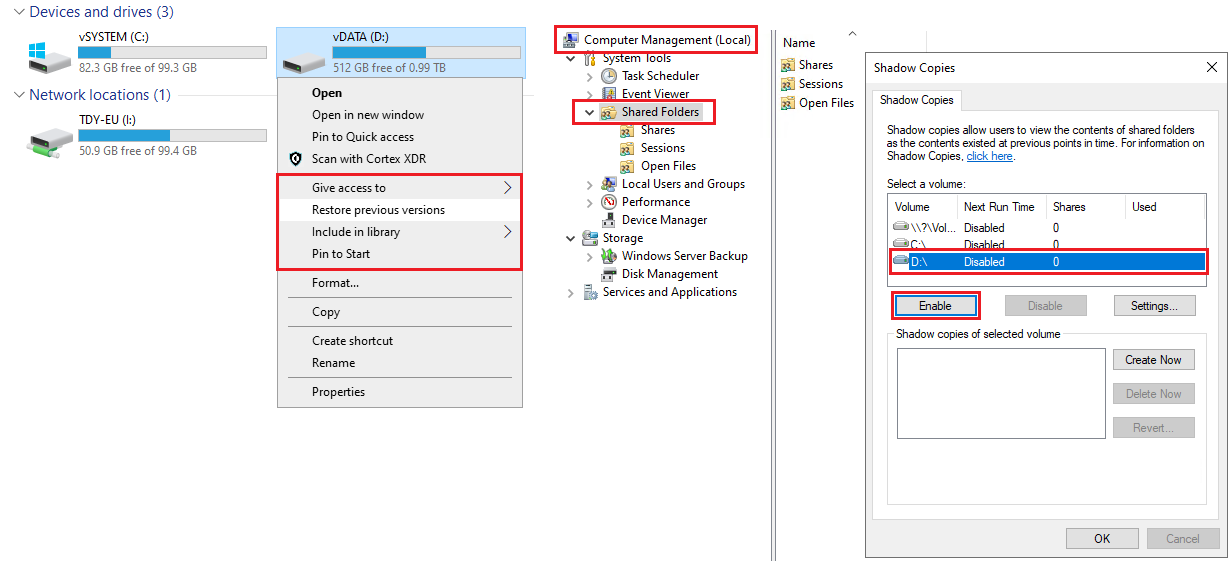
Windows Shadow Copies
Shadow copies take up space in C:\System Volume Information (Hidden Folder) They can be reduced or completely deleted using VSSAdmin
Shows Shadow Copy Versions:
vssadmin list shadowstorage
Deletes all Shadow Copies:
vssadmin delete shadows /all
BranchCache “PeerDistRepub” folder
BranchCache is basically a cached version of updates from Microsoft. Folder can be flushed/cleared using netsh
Check Cache
netsh branchcache show status all
Flush Cache
netsh branchcache flush
Uninstall BranchCache Feature (PowerShell)
Uninstall-WindowsFeature Branchcache